Imagine this: you're sitting in your cozy living room, sipping coffee, and suddenly you need to access your IoT devices from miles away. How do you make it happen without compromising security? Well, buckle up, because we're diving deep into the world of securely connecting remote IoT devices using P2P SSH on a Raspberry Pi. This isn't just any guide—it's your one-stop solution to mastering this tech-savvy skill.
Connecting remote IoT devices isn’t as simple as plugging in a cable anymore. With the rise of smart homes, wearable tech, and industrial automation, ensuring secure communication between devices is more critical than ever. Today, we’re going to break down how you can set up a peer-to-peer (P2P) SSH connection on a Raspberry Pi, making it possible to download and manage data remotely while keeping everything locked down tight.
Whether you're a hobbyist, a professional developer, or someone who just wants to tinker with their Raspberry Pi, this guide will arm you with the knowledge and tools to securely connect your IoT devices. So grab your favorite drink, and let’s get started!
Read also:Why Emily Rudd Is A Rising Star In The Entertainment Industry Today
Table of Contents
Introduction: Why Secure Connections Matter
Raspberry Pi Basics: What You Need to Know
Setting Up SSH on Raspberry Pi
Securing Your Remote Connections
Read also:Teresa Capone The Rising Star Whorsquos Taking The World By Storm
Remote Access: Downloading Data Securely
Advanced Techniques for Enhanced Security
Why Secure Connections Matter
In today's hyper-connected world, IoT devices are everywhere. From smart fridges to autonomous drones, these gadgets are revolutionizing how we live and work. But with great power comes great responsibility. If you're not careful, leaving your IoT devices exposed can lead to serious security breaches.
That’s where SSH comes in. Secure Shell (SSH) is like a digital lock for your devices. It encrypts your data and ensures that only authorized users can access your systems. By setting up a secure P2P SSH connection on a Raspberry Pi, you can remotely manage your IoT devices without worrying about hackers or unauthorized access.
But why use a Raspberry Pi? Well, it's affordable, versatile, and perfect for DIY projects. Plus, it's easy to configure and has a massive community of users who share tips, tricks, and tutorials. So whether you're a tech newbie or a seasoned pro, the Raspberry Pi is a fantastic choice for building secure IoT networks.
Raspberry Pi Basics: What You Need to Know
Before we dive into the nitty-gritty of setting up SSH, let's take a quick look at what makes the Raspberry Pi so special. The Raspberry Pi is a single-board computer that's small enough to fit in your pocket but powerful enough to run complex applications. Here are some key points to keep in mind:
- Compact Size: The Raspberry Pi is lightweight and portable, making it ideal for IoT projects.
- Cost-Effective: You can pick up a Raspberry Pi for under $50, depending on the model.
- Open-Source: The Raspberry Pi runs on Linux-based operating systems, which means you have access to a wide range of software and tools.
- Community Support: With millions of users worldwide, finding help or inspiration is as easy as searching online.
If you're new to the Raspberry Pi, don't worry! There are tons of resources available to help you get started. From setting up your operating system to configuring your hardware, the learning curve isn't as steep as you might think.
Choosing the Right Raspberry Pi Model
Not all Raspberry Pi models are created equal. Depending on your project requirements, you may want to choose a specific version. Here's a quick rundown of the most popular models:
- Raspberry Pi 4: The latest and greatest, with faster processing power and more RAM options.
- Raspberry Pi 3: A solid choice for most IoT projects, offering good performance at an affordable price.
- Raspberry Pi Zero: Tiny and budget-friendly, perfect for lightweight applications.
For our purposes, the Raspberry Pi 4 is the best option due to its speed and compatibility with modern software. However, if you're working on a smaller-scale project, the Raspberry Pi 3 or Zero could work just as well.
IoT and SSH: An Overview
Now that we've covered the basics of the Raspberry Pi, let's talk about IoT and SSH. The Internet of Things (IoT) refers to the network of physical devices embedded with sensors, software, and connectivity features. These devices exchange data and interact with each other, creating a smart ecosystem.
SSH, or Secure Shell, is a cryptographic protocol used to secure communications between devices. It provides encrypted connections, ensuring that sensitive information remains private. By combining IoT with SSH, you can create a secure, reliable way to manage your devices remotely.
Here are some benefits of using SSH for IoT:
- Encryption: SSH encrypts all data transmitted between devices, protecting against eavesdropping and interception.
- Authentication: SSH uses public-key cryptography to verify the identity of users and devices.
- Remote Command Execution: With SSH, you can execute commands on remote devices as if you were sitting right in front of them.
While SSH is a powerful tool, it's not without its challenges. Proper configuration and security measures are essential to avoid vulnerabilities. In the next section, we'll explore P2P connections and how they fit into the picture.
Understanding P2P Connections
Peer-to-peer (P2P) connections allow devices to communicate directly with each other without relying on a central server. This setup is particularly useful for IoT applications, where latency and bandwidth are critical factors.
When you establish a P2P SSH connection, your Raspberry Pi acts as a bridge between your local network and remote devices. This setup eliminates the need for additional infrastructure, making it cost-effective and efficient.
Here are some advantages of using P2P connections:
- Reduced Latency: Direct connections mean faster data transfer and lower delays.
- Scalability: P2P networks can grow dynamically, accommodating more devices as needed.
- Reliability: Without a central server, your system is less prone to single points of failure.
However, setting up a P2P SSH connection requires careful planning and configuration. In the following sections, we'll walk you through the steps to ensure a secure and stable connection.
Securing Your P2P Network
Security is paramount when working with P2P connections. To protect your network, consider implementing the following measures:
- Use Strong Passwords: Avoid using default credentials and opt for complex, unique passwords.
- Enable Two-Factor Authentication (2FA): Add an extra layer of security by requiring a second form of verification.
- Regularly Update Software: Keep your operating system and applications up to date to patch vulnerabilities.
By taking these precautions, you can significantly reduce the risk of unauthorized access and ensure the integrity of your IoT network.
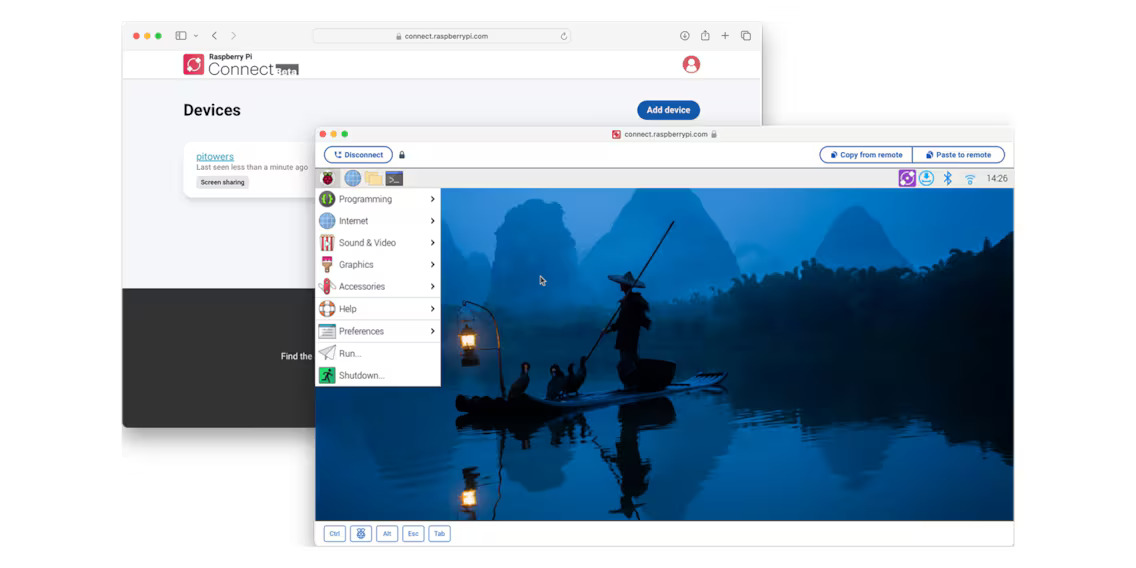
Setting Up SSH on Raspberry Pi
Now it's time to roll up our sleeves and get to work. Setting up SSH on a Raspberry Pi is relatively straightforward, but it does require a bit of technical know-how. Follow these steps to configure SSH on your device:
- Enable SSH: Depending on your operating system, SSH may already be enabled. If not, you can enable it by running the command `sudo raspi-config` and selecting the SSH option.
- Generate SSH Keys: Use the `ssh-keygen` command to create a pair of public and private keys. This will allow you to authenticate without entering a password every time.
- Configure Firewall Settings: Adjust your firewall rules to allow SSH traffic on port 22 (or a custom port if you prefer).
- Test the Connection: Use the `ssh` command followed by your device's IP address to verify that everything is working correctly.
With SSH up and running, you're ready to move on to the next step: securing your connections.
Securing Your Remote Connections
Securing your SSH connections is essential to prevent unauthorized access. Here are some best practices to keep your network safe:
- Disable Password Authentication: Instead of using passwords, rely on SSH keys for authentication.
- Change the Default Port: Moving SSH from port 22 to a non-standard port can deter automated attacks.
- Limit User Access: Restrict SSH access to specific users or IP addresses to minimize the attack surface.
In addition to these measures, consider using tools like Fail2Ban to automatically block malicious login attempts. By implementing these strategies, you can create a robust defense against potential threats.
Choosing the Right Encryption Methods
Encryption is the backbone of secure SSH connections. When configuring your Raspberry Pi, choose strong encryption algorithms such as AES-256 or ChaCha20. These algorithms provide excellent protection against eavesdropping and data theft.
Remember, encryption is only as strong as its weakest link. Always ensure that both your local and remote devices are using the latest encryption protocols to maintain the highest level of security.
Remote Access: Downloading Data Securely
One of the primary benefits of SSH is the ability to download data securely from remote devices. Whether you're retrieving sensor readings, log files, or configuration backups, SSH ensures that your data remains protected during transmission.
To download files using SSH, you can use the `scp` (secure copy) command. For example, to copy a file from your Raspberry Pi to your local machine, you would run:
`scp username@raspberrypi:/path/to/file /local/path`
This command securely transfers the file while encrypting the connection. You can also use tools like WinSCP or FileZilla for a more user-friendly interface.
Managing Large Data Sets
When dealing with large data sets, consider compressing your files before transferring them. This reduces transfer times and minimizes bandwidth usage. Tools like `gzip` or `tar` can help you compress and archive files for easier handling.
Additionally, schedule regular backups to ensure that your data is always up to date and recoverable in case of a failure. By automating these processes, you can focus on more critical tasks while your system handles routine maintenance.
Troubleshooting Common Issues
No matter how careful you are, issues can arise when setting up SSH on a Raspberry Pi. Here are some common problems and their solutions:
- Connection Refused: Check your firewall settings and ensure that SSH is enabled on your device.
- Authentication Failed: Verify that your SSH keys are correctly configured and that you're using the right username.
- Slow Transfer Speeds: Optimize your network settings and consider using a faster connection if possible.
If you're still stuck, don't hesitate to reach out to the Raspberry Pi community for support. With thousands of users worldwide, chances are someone else has encountered—and solved—the same issue.
Advanced Techniques for Enhanced Security
For those looking to take their security game to the next level, here are some advanced techniques to consider:
- Use a Hardware Security Module (HSM): An HSM adds an extra layer of protection by storing cryptographic keys in a secure, tamper-resistant device.
- Implement Network Segmentation: